Email Triage
Overview
Disclaimer: This is not aimed at delivering the level of supporting computer science knowledge and self study is a requirement to obtain profficiency.
Scope
The purpose of this tutorial is to demonstrate the logic flow when triaging suspicious emails. With practice the student will become familiar with the email structure and how to identify key information when understanding the content and header of the email file format as part of triage process.
Required Tooling
- MSGConvert
- oledump.py
- wget
- pdf-parser
- web browser
- text editor
- base64
Learning Outcome
The student will be able to manually parse an email file and extract header values and inspect individual elements of the email object. The student will be able to identify valuable information and possible next steps.
Competency
Level: Basic, Difficulty: Easy, Computer Science: Email file format
Competancy Areas:
- Computer Network Defense - Knowledge of malware analysis concepts and methodology.
- Infrastructure Design - Knowledge of how traffic flows accros a network (e.g., TCPIP, OSI, ITIL).
- Computer Network Defense - Skill in protecting against malware.
- Operating Systems - Knowledge of file extensions and formats.
Topic
When processing suspicious emails there are a number of technology based solutions that can provide a level of abstraction and a facade from the the computer science element. It is important that the responder understands the email structure and is able to manually parser susupect emails.
The iniital assessment can be performed visually using MSGViewer which also allows header inspection.
When reviewing header understanding of the different fields and which are of relevance to the email flow and response process is important.
Elements such as Recieved by, x-sender, message header there are also some inline tools that modify the header during transit which can also contribute in this case fireeye and ironports.
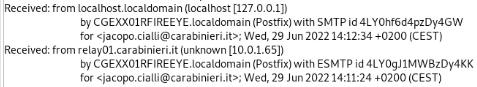
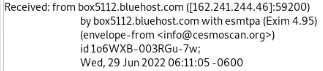
These help the responder understand the journey the email has taken and extract indicators of intelligence that may help responding or further detection.
Once the file is reviewing in eml format the structure is easy to navigate with oledump or a text editor. locating the base64 encoded sections is straight forward and this allows manual extraction and decoding used a text editor and base64 decoder.
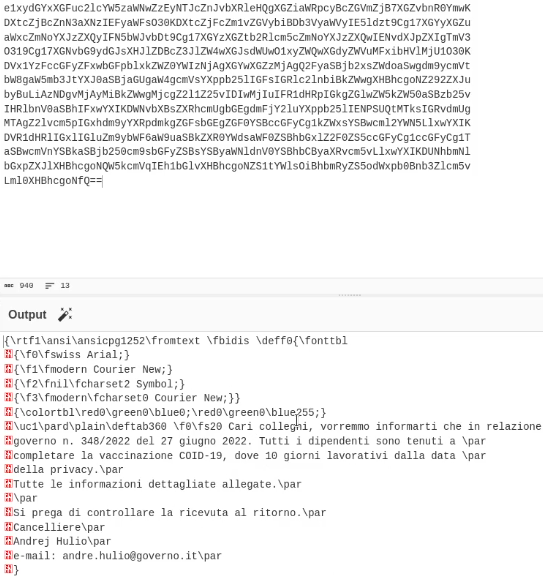
This results in the attached PDF file. This can then be parsed with pdf-parser to under stand the container contents. IN this case it allowed the identifcation of the next stop URL. These files can be opened but any active content may also execute.
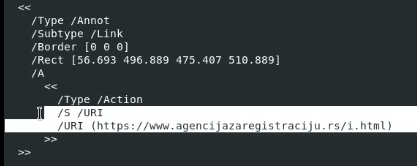
In this case wget would be used to obtained i.html to continue with analysis however due to use by date this file was not longer available.
Video
Duration:15min
Further Reading Subjects:
- eml file format
- msg file format
- PDF file format
- email header